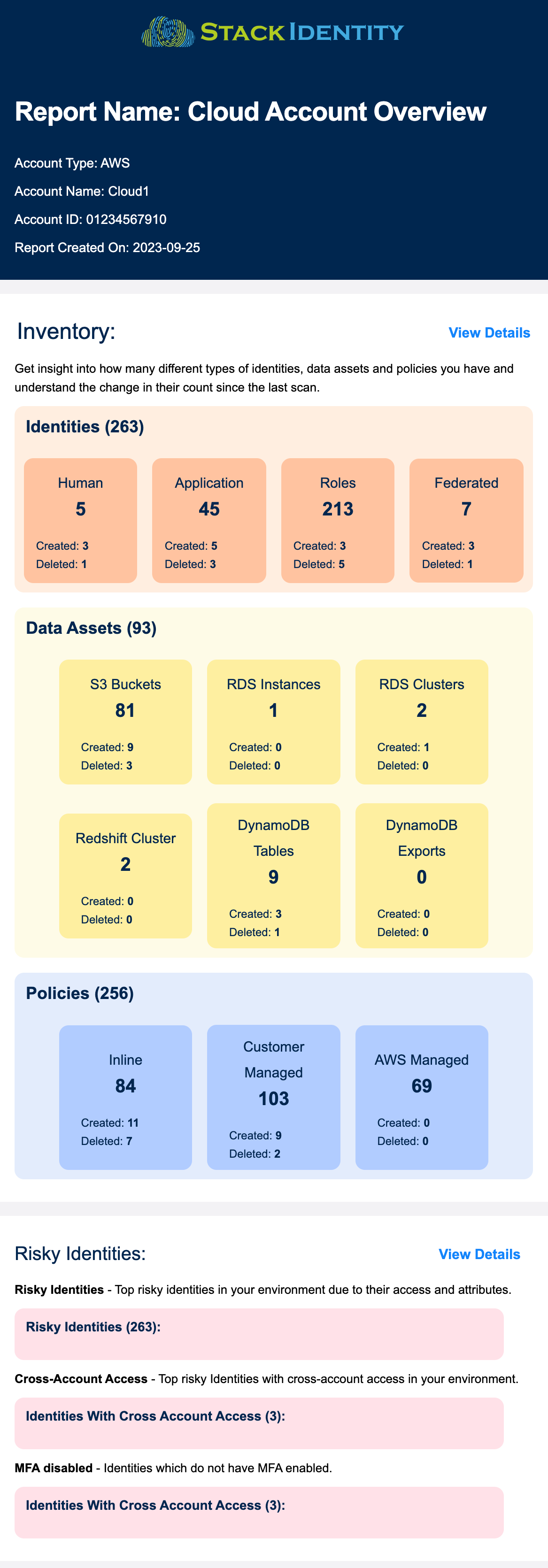
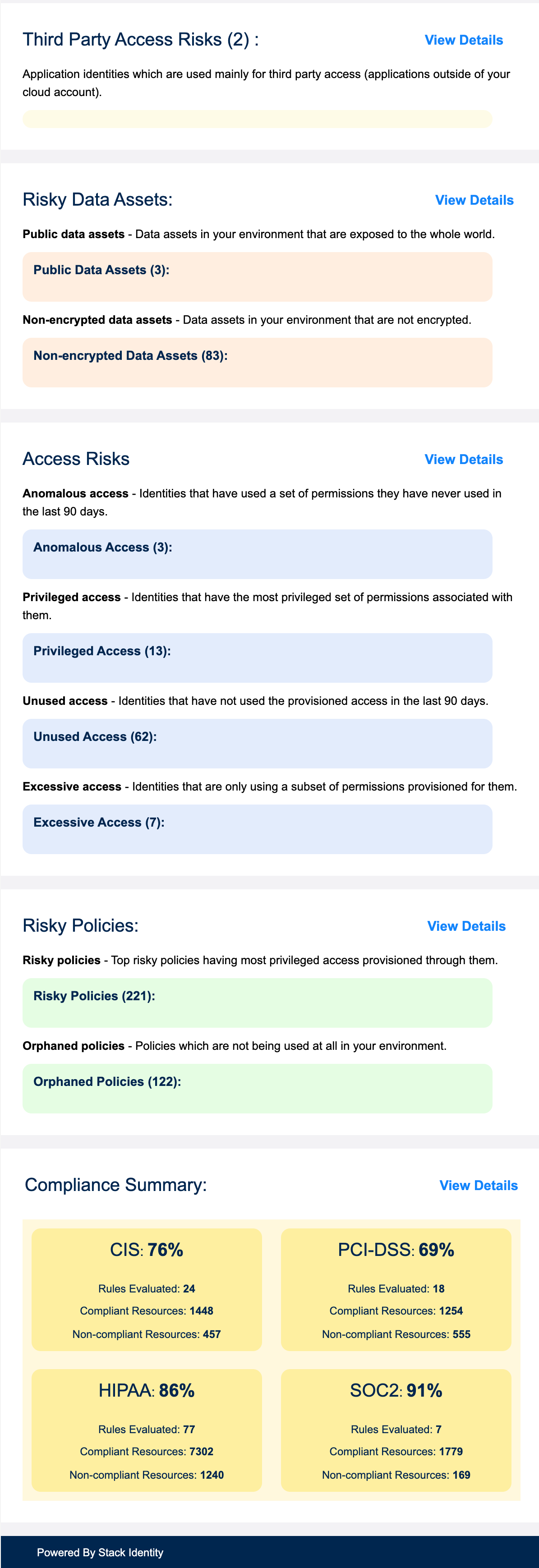
Register for your Shadow Access Risk Assessment
Sign up for Shadow Access Risk Assessment (SARA) and detect the 10 types of Shadow Access in your cloud.
On a daily basis, SARA provides a prioritized list of operational exposures and data exfiltration risks based on Stack identity’s patent pending Breach Prediction Index (BPI).
Run SARA in your cloud environment to know:
- How many identities, data assets and policies do you have today?
- Top risky identities due to their access and entitlements
- Which data assets in your environment are exposed?
- Which identities have unused permissions?
- Daily compliance scorecard for CIS, PCI-DSS, SOC2 and HIPAA
Install Stack Identity’s Shadow Access Risk Assessment (SARA) to discover the identity security risks in your cloud creating operational risks, IAM weaknesses, and generating Zero Trust blind spots.